- Home
- Knox Law Institute
- Publications
- General Password Practices and Protections
General Password Practices and Protections
Author: Mark A. Denlinger
Originally published in October 2018
Copyright © 2018 Knox McLaughlin Gornall & Sennett, P.C.
Heading Access to / Theft of Passwords is one of the leading causes of data breaches and Identity Theft
Too many passwords are predictable and follow familiar patterns
If given enough time, hackers can crack many passwords in a matter of days or even hours. People/companies use familiar patterns – foreign words, movie or book titles, names or places, address numbers or phone numbers, or patterns on a keyboard, etc.
Strong Passwords have 2 Things in Common
They avoid patterns, and they are too long for a brute-force attack to succeed.
General Concepts to Boost Password Protections
- Stop making sense: Use unrelated words or numbers. Pick several long, random words and string them together into a nonsensical sentence.
- Use a Password Manager: Password managers can generate complex, unique passwords for each account. But you still need one solid, well-crafted password for your password manager account.
- It is Ok to Write it Down, but: Keep them in a secure location and/or locked up. Don’t just write them on Post-It notes all around your desk, computer, etc.
- Planning Idea: leave a sealed envelope list of passwords with your legal counsel/accountant or in a lockbox or fireproof safe in case of death or destruction/catastrophe.
- Change It Often vs. Remaining Password Loyal: Most experts recommend you change your passwords regularly – anywhere from any 6 months to every 18 months. Some accounts/log-ins require and force you to change your passwords on a regular basis.
- However, sticking with a good, strong password is not always a “bad thing” because if you have to switch often, there is a tendency to make the passwords weaker and weaker (since you know it will change again).
Specific Tips and Suggestions for Creating (and Memorizing) Passwords
- Use “LeetSpeak” (or “1337”Speak or “eleet”) – it is system of modified spellings and verbiage used primarily on the Internet for many phonetic languages. It uses some ASCII characters to replace Latin characters in ways that play on the similarity of their glyphs via reflection or other resemblance.
- Common LeetSpeak substitutions:
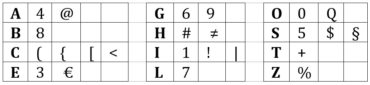
- Example: “YankeesRule” becomes “Y@nk33$Ru73”
- Combine words – string a series of random words together and combine with LeetSpeak. Select words not normally associated with each other, and use LeetSpeak and/or special characters to enhance protection.
- Example: Combine “Math” and “Sassafras” to make “Math/Sassafras”, and then adjust to make “M4+#/54554fr45”
- Remove vowels - Certain written languages, such as Hebrew or Arabic, do not use vowels, and thus it is simple to create a complex passphrase in English by dropping the vowels, as well as use LeetSpeak and/or special characters to increase protection.
- Example: Make “KnoxLawInstituteRocks!” into “KnxLwnstttRcks!”, and if you need to have a number to meet password requirements, then you can always add a number, such as “KnxLwnstttRcks!9”
- Reverse words - While slightly more complicated, it is useful in that it is easy to remember – since it is the key word or words backwards – and can combine with LeetSpeak and/or special characters.
- Example: “Trepidation” becomes “Noitadipert”, and you can build upon it by making it “N01+4d1p3r+”
- Use phrase or sentence - This is best way to create a passphrase when combined with LeetSpeak substitution and this technique can create an easily remembered but complex passphrase.
- Example: A phrase like “MyKungFuIsStrongerThanYours” into a variation like “MyKun6Fu1$$+r0n63r+#@nY0ur$”
Author: Mark A. Denlinger
Originally published in October 2018
Copyright © 2018 Knox McLaughlin Gornall & Sennett, P.C.

